

ROUTING PROTOCOLS
Routing protocols are like the GPS systems of computer networks. They help routers—devices that direct traffic on the internet—find the best paths for sending data from one place to another.
These protocols come in different types, each with its own way of figuring out the most efficient routes. Let’s explore these routing protocols and their types in unique and basic English, covering the essentials you need to know.
Introduction to Routing Protocols:
Imagine you’re planning a road trip and need to map out the best route to reach your destination. In the world of computer networks, routing protocols do something similar.
They help routers decide how to send data packets to their intended destinations across a network of interconnected devices. Without routing protocols, routers would be like lost travelers without a map, unsure of which path to take.
Types of Routing Protocols:
Routing protocols can be classified into several types based on their operation and characteristics. Here are the main types:
Distance Vector Protocols:
Distance vector protocols work by routers sharing information about the distance and direction to reach different destinations. Each router sends periodic updates to its neighbors, informing them of the routes it knows about. Examples of distance vector protocols are
- Routing Information Protocol (RIP)
2. Interior Gateway Routing Protocol (IGRP) etc
Link-State Protocols:
Link-state protocols focus on sharing detailed information about the topology, or structure, of the network. Routers exchange “link-state advertisements” (LSAs) containing information
about their directly connected neighbors and the cost of reaching them. This allows each router to build a comprehensive map of the network.
Examples of Link-state Protocols
- Open Shortest Path First (OSPF)
- (IS-IS) Intermediate System – Intermediate System etc
Path Vector Protocols:
Path vector protocols, like the Border Gateway Protocol (BGP), are used in large-scale networks, such as the internet. Instead of just considering distance or cost, path vector protocols take into account various path attributes, policies, and rules when making routing decisions.
This makes them highly adaptable to complex network environments and allows for fine-grained control over routing decisions.
Hybrid Protocols:
Hybrid protocols combine elements of both distance vector and link-state protocols to leverage their respective advantages. Example of Hybrid Protocol is Enhanced Interior Gateway Routing Protocol (EIGRP).
It shares some characteristics with distance vector protocols but also incorporates features like rapid convergence and efficient use of bandwidth found in link-state protocols.
ROUTING INFORMATION PROTOCOL (RIP)
Routing Information Protocol (RIP) is like a messenger bird that flies around the internet, carrying messages between different places. Imagine you have a map of a city with various destinations marked on it. Now, suppose you want to send a letter from your house to a friend’s house. You need to decide the best route for your letter to reach its destination.
In the world of computer networks, RIP serves a similar purpose. It helps routers, which are like traffic directors on the internet, to find the best path for data packets to travel from one place to another. These data packets are like the letters you send in the mail, containing information that needs to reach its destination.
Here’s how RIP works in a nutshell:
Sharing Information: Just like you would consult a map to find the best route, routers in a network need information about the different paths available to reach various destinations. RIP routers exchange information about these paths with each other.
Counting Hops: In RIP, the “distance” between routers is measured in hops. A hop is like a step or jump from one router to another. Each time a packet passes through a router, it’s counted as one hop. RIP keeps track of these hops to determine the shortest path to a destination.
Choosing the Best Path: RIP routers compare the information they receive from their neighbors to find the shortest path to each destination. They update their routing tables accordingly, always aiming to minimize the number of hops required to reach a destination.
Periodic Updates: Networks are dynamic, with routers coming online, going offline, or experiencing changes in connectivity. To adapt to these changes, RIP routers regularly exchange updates to keep their routing information current.
Timeouts and Metrics: If a router doesn’t receive updates from its neighbors for a certain period, it assumes that the connection is no longer valid. It then removes that route from its routing table. RIP also uses metrics, like the time it takes for a packet to travel a route, to determine the best path when multiple routes are available.
Convergence: RIP aims for convergence, which means that all routers in the network have consistent and up-to-date routing information. This ensures that data packets can reach their destinations efficiently without getting lost or delayed.
Now, let’s delve into some unique aspects of RIP:
Historical Significance: RIP is one of the oldest routing protocols still in use today. It dates back to the early days of the internet, when networks were smaller and simpler. Despite its age, RIP remains relevant in certain scenarios, particularly in small to medium-sized networks where simplicity is valued over complexity.
Distance Vector Protocol: RIP belongs to a class of routing protocols known as distance vector protocols. In simple terms, this means that routers make routing decisions based on the “distance” to a destination, where distance is measured in terms of hops. While effective in small networks, distance vector protocols like RIP can suffer from limitations such as slow convergence and susceptibility to routing loops in larger, more complex networks.
Maximum Hop Count: Routing Information Protocol (RIP) has a max. hop count upto 15. This means that it can only support networks where the maximum number of hops between any two routers is 15 or fewer. If a route exceeds this hop count, RIP considers it unreachable. While this limitation may seem restrictive, it helps prevent routing loops and ensures that RIP converges efficiently within its supported scope.
Broadcast Updates: RIP routers use broadcast messages to exchange routing information with their neighbors. This means that when a router updates its routing table, it sends that information to all other routers in the network. While broadcast updates simplify the process of sharing routing information, they can also consume network bandwidth, especially in larger networks with many routers.
Triggered Updates: In addition to periodic updates, RIP routers send triggered updates when certain events occur, such as a change in network topology or the failure of a router or link. These triggered updates help expedite the convergence process by immediately informing neighboring routers of relevant changes.
Authentication: To ensure the security and integrity of routing information, modern implementations of RIP support authentication mechanisms. These mechanisms allow routers to verify the identity of neighboring routers and validate the authenticity of routing updates. By preventing unauthorized devices from injecting false routing information into the network, authentication helps safeguard against routing attacks and unauthorized access.
RIPng: As the internet evolved and IPv6 became more prevalent, an extension of RIP called RIPng (Routing Information Protocol Next Generation) was developed to support the IPv6 addressing scheme. RIPng retains many of the core principles of RIP while adapting to the larger address space and other features introduced by IPv6.
In conclusion, Routing Information Protocol (RIP) is a fundamental routing protocol that has played a significant role in the development of computer networks. Despite its simplicity and age, RIP continues to be used in various environments, particularly in smaller networks where ease of implementation and management are priorities. By understanding how RIP works and its unique characteristics, network administrators can effectively design and manage their networks to ensure efficient and reliable data communication.
ROUTING INFORMATION PROTOCOL VERSION 2 (RIP V2)
RIP version 2 (RIPv2) is like an upgraded messenger bird for the internet. It’s an improved version of the Routing Information Protocol (RIP), designed to overcome some limitations of the original RIP while still keeping things simple.
Here are some unique things about RIP version 2:
Support for IPv6: RIPv2 can handle the newer IPv6 addresses, which are becoming more common as the internet grows. This means it can guide data packets using these longer, more complex addresses.
Multicast Updates: Instead of broadcasting updates to every router on the network like RIP, RIPv2 sends updates to a specific group of routers. It’s like sending a message to a select group of friends instead of shouting it out to everyone in town. This saves bandwidth and makes the network more efficient.
Authentication: RIPv2 offers a way to verify that the updates it receives are from trusted sources. It’s like checking the sender’s ID before accepting a package. This helps prevent unauthorized routers from messing with the network’s routing information.
Variable-Length Subnet Masks (VLSM) Support: RIPv2 can handle different subnet mask lengths for different network segments. It’s like being able to use smaller or larger envelopes depending on how much you need to send. This flexibility allows for more efficient use of IP addresses.
Backward Compatibility: Despite its enhancements, RIPv2 can still work with routers that use the older RIP version 1. It’s like being able to talk to both old and new friends using the same language.
In simple terms, RIP version 2 is like a smarter and more secure messenger bird that can handle bigger crowds and new addresses, making it a reliable guide for data traveling across the internet.

ENHANCED INTERIOR GATEWAY ROUTING PROTOCOL (EIGRP)
Introduction to EIGRP:
Imagine you’re in a bustling city, trying to navigate the streets to reach your destination. Each street has its own traffic flow, and you need to choose the fastest route to get where you’re going. In the world of computer networks, routers face a similar challenge. They need to determine the best paths for data to travel through the network efficiently. That’s where Enhanced Interior Gateway Routing Protocol (EIGRP) comes in.
What is EIGRP?
EIGRP is like a super-smart GPS system for computer networks. It’s a routing protocol that helps routers make intelligent decisions about the best routes for data packets to travel. Developed by Cisco, EIGRP is designed to be fast, efficient, and adaptable to various network conditions.
How Does EIGRP Work?
Neighborship and Hello Packets: EIGRP routers form “neighborships” with their neighboring routers. It’s like making friends with the people living next door. They exchange small packets called “hello packets” to establish and maintain these neighborships. This ensures that routers know who their neighbors are and can communicate with them effectively.
Topology Table: Each EIGRP router maintains a topology table, which is like a map of the network. It stores information about all the routes that the router knows about, including the next hop router and the metric (cost) associated with each route. This information helps the router make informed decisions about the best paths to reach different destinations.
Feasible Distance and Reported Distance: In EIGRP, routers use two metrics to determine the best routes: feasible distance and reported distance. Feasible distance is the total cost of reaching a destination, while reported distance is the cost reported by a neighboring router. Routers select the route with the lowest feasible distance as the best path to the destination.
Successor and Feasible Successor: EIGRP routers maintain backup routes called “feasible successors” in addition to their primary routes called “successors.” Feasible successors are alternative paths to reach a destination that have a cost lower than the current best path. If the primary route fails, the router can quickly switch to a feasible successor without having to recalculate the entire routing table.
DUAL Algorithm: EIGRP uses a sophisticated algorithm called the Diffusing Update Algorithm (DUAL) to calculate the best routes. DUAL ensures that routers converge quickly to optimal routes while avoiding routing loops and unnecessary traffic.
Update and Query Messages:EIGRP routers exchange routing information using update messages. When a change occurs in the network, such as a link failure, routers send query messages to their neighbors to determine if they have alternative routes to the affected destination. This helps routers quickly adapt to changes in the network topology.
Partial Updates: EIGRP is efficient in its use of bandwidth. Instead of sending complete routing updates periodically, it only sends updates when there is a change in the network. This reduces unnecessary traffic and conserves network resources.
Unique Aspects of EIGRP:
Hybrid Protocol: EIGRP combines the best features of both distance vector and link-state routing protocols. It behaves like a distance vector protocol in terms of its method for calculating routes but uses some aspects of link-state protocols for maintaining neighbor relationships and exchanging routing information. This hybrid approach makes EIGRP highly adaptable to different network environments.
Fast Convergence: EIGRP is known for its rapid convergence time. When a change occurs in the network, such as a link failure or the introduction of a new route, EIGRP routers can quickly recalculate their routing tables and converge to optimal routes. This ensures minimal disruption to network traffic and faster recovery from network failures.
Low Bandwidth Usage:EIGRP is designed to be bandwidth-efficient. It uses small hello packets for neighbor discovery and updates only when necessary. This reduces the amount of overhead traffic on the network, making EIGRP suitable for networks with limited bandwidth.
Scalability: EIGRP is scalable and can be used in networks of varying sizes, from small office networks to large enterprise networks. It can handle hundreds or even thousands of routers without sacrificing performance or efficiency. This scalability makes EIGRP a versatile choice for network administrators managing networks of different scales.
Cisco’s Proprietary Protocol: EIGRP is developed and owned by Cisco Systems, one of the leading networking companies in the world. While EIGRP is widely used in Cisco environments, it is not an open standard like OSPF (Open Shortest Path First) or RIP (Routing Information Protocol). This means that EIGRP can only be implemented on Cisco devices, limiting its interoperability with devices from other vendors.
Conclusion:
Enhanced Interior Gateway Routing Protocol (EIGRP) is a powerful and versatile routing protocol that plays a crucial role in modern computer networks. With its fast convergence, efficient use of bandwidth, and scalability, EIGRP helps routers make intelligent routing decisions and ensures optimal performance and reliability of network communication. While primarily used in Cisco environments, EIGRP’s unique features and capabilities make it a popular choice for network administrators looking to build robust and efficient networks.
OPEN SHORTEST PATH FIRST PROTOCOL
For example you are planning a road trip across the country. You need to map out the best route, considering factors like distance, traffic, and road conditions. In the world of computer networks, routers face a similar challenge—they need to determine the best paths for data to travel through the network efficiently. That’s where OSPF comes in.
What is OSPF?
OSPF, or Open Shortest Path First, is like a traffic manager for computer networks. It’s a routing protocol that helps routers find the shortest and most reliable paths for data packets to reach their destinations. OSPF is widely used in large-scale networks, such as corporate networks and the internet backbone, to ensure efficient and robust communication.
How Does OSPF Work?
Link-State Routing: OSPF is a link-state routing protocol, which means routers exchange information about the state of their links with each other. Instead of just knowing the distance to a destination (like in distance vector routing protocols), OSPF routers have a detailed map of the entire network, showing all the links and their statuses.
Hello Packets: OSPF routers use “hello packets” to discover and maintain neighbor relationships. When routers first connect to the network, they send out hello packets to find other routers nearby. Once they’ve identified their neighbors, they periodically exchange hello packets to ensure they’re still connected.
Link-State Advertisements (LSAs): OSPF routers send out link-state advertisements (LSAs) to share information about their links with their neighbors. These LSAs contain details such as the router’s ID, the links it’s connected to, and the state of those links (like whether they’re up or down).
Building the Link-State Database: Each OSPF router collects LSAs from its neighbors and uses them to build a link-state database. This database contains a comprehensive view of the network, including all the routers and links. Using this database, OSPF routers can calculate the shortest paths to reach each destination.
Dijkstra’s Shortest Path Algorithm: OSPF routers use Dijkstra’s Shortest Path First (SPF) algorithm to calculate the shortest paths through the network. This algorithm considers the costs associated with each link (such as bandwidth or delay) to determine the most efficient routes. By finding the shortest paths to all destinations, OSPF ensures optimal routing throughout the network.
Routing Table Calculation: Once OSPF routers have calculated the shortest paths, they use this information to populate their routing tables. The routing table contains entries for all reachable destinations, along with the next-hop router and the interface to reach each destination. By consulting the routing table, routers can forward data packets along the most appropriate paths.
Dynamic Updates: OSPF is dynamic and adaptive—it responds to changes in the network topology in real-time. If a link goes down or a new router is added to the network, OSPF routers quickly update their link-state databases and recalculate the shortest paths. This ensures that routing decisions are always based on the most current information.
Unique Aspects of OSPF:
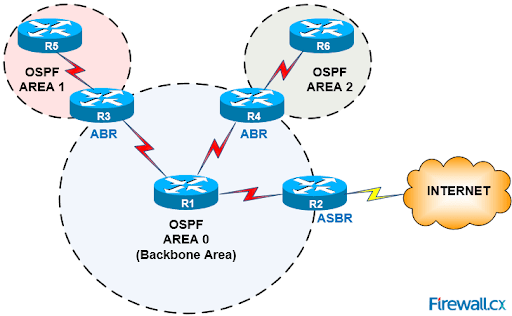
Hierarchical Design: OSPF networks are often organized into a hierarchical structure, with routers grouped into areas. This hierarchical design helps manage the complexity of large networks by dividing them into smaller, more manageable units. It also reduces the amount of routing information that needs to be exchanged between routers, improving scalability and performance.
Areas and Backbone Area: OSPF networks consist of multiple areas, each with its own set of routers and links. All areas are connected to a central area called the backbone area (Area 0). The backbone area serves as the core of the OSPF network, providing connectivity between different areas. This hierarchical design improves network scalability and reduces the impact of topology changes on the entire network.
Link-State Database Synchronization: OSPF routers maintain synchronized link-state databases within the same area. This means that all routers in the area have an identical view of the network topology, allowing them to make consistent routing decisions. Link-state database synchronization is achieved through the exchange of LSAs between routers, ensuring that each router has the latest information about the network.
Route Summarization: OSPF supports route summarization, which involves aggregating multiple routes into a single summary route. This helps reduce the size of the routing tables and minimize the amount of routing information exchanged between routers. Route summarization is particularly useful in large networks with many subnets, where it can significantly improve routing efficiency.
Authentication: OSPF supports authentication to ensure the security and integrity of routing information. Routers can use authentication mechanisms such as plaintext passwords or cryptographic authentication to verify the identity of OSPF neighbors and validate the authenticity of routing updates. Authentication helps prevent unauthorized routers from injecting false routing information into the network, enhancing network security.
Multi-Area OSPF: OSPF can scale to large networks through the use of multiple areas. Multi-Area OSPF divides the network into separate areas, each with its own link-state database and routing tables. This allows OSPF to scale to networks of virtually any size while maintaining efficient routing and fast convergence.
Support for IPv6: OSPF is fully compatible with IPv6, the next-generation Internet Protocol. It supports IPv6 addressing and routing, allowing OSPF networks to seamlessly transition to IPv6 without any major changes to the routing infrastructure. This ensures that OSPF remains relevant and future-proof in the evolving landscape of networking technologies.
Conclusion:
Open Shortest Path First (OSPF) is a robust and scalable routing protocol that plays a critical role in modern computer networks. By using link-state routing and Dijkstra’s algorithm, OSPF routers can calculate the shortest paths through the network, ensuring efficient and reliable data communication. With its hierarchical design, support for route summarization, and compatibility with IPv6, OSPF is well-suited for large-scale networks with complex topologies. As networks continue to evolve, OSPF remains a cornerstone of routing protocols, providing the foundation for efficient and resilient communication in diverse network environments.


INTERMEDIATE SYSTEM-TO-INTERMEDIATE SYSTEM (IS-IS)
Intermediate System-to-Intermediate System (IS-IS) is a routing protocol used in computer networks to efficiently exchange routing information between routers. It’s like a system of road signs and traffic lights that helps guide data packets through the network, ensuring they reach their destination quickly and reliably. Let’s explore IS-IS in simple terms, including its unique features and how it works.
Introduction to IS-IS:
Imagine you’re driving on a highway network with multiple intersections and junctions. You need clear signs and signals to navigate through the network and reach your destination safely. Similarly, in a computer network, routers need a reliable method to determine the best paths for data packets to travel. IS-IS provides this functionality by enabling routers to exchange routing information and calculate optimal routes through the network.
What is IS-IS?
IS-IS, or Intermediate System-to-Intermediate System, is a routing protocol designed to facilitate communication between routers in a network. It operates at the OSI (Open Systems Interconnection) Layer 2 and Layer 3, making it suitable for both local and wide-area networks. IS-IS is particularly popular in large-scale networks, such as internet service provider (ISP) backbones and telecommunications networks.
How Does IS-IS Work?
Adjacencies and Hello Packets: IS-IS routers establish adjacencies with their neighboring routers to exchange routing information. It’s like making friends with your neighbors so you can share information with each other. Routers send “hello packets” to discover and maintain these adjacencies, ensuring they can communicate effectively.
Link-State Database: Each IS-IS router maintains a link-state database containing information about the network’s topology. This database includes details about the router’s neighbors, the links connecting them, and their associated metrics (costs). By sharing this information, routers build a comprehensive view of the network’s structure and available paths.
SPF Algorithm: IS-IS routers use the Shortest Path First (SPF) algorithm to calculate the shortest paths through the network. This algorithm evaluates the costs of different paths and selects the most efficient routes to reach each destination. By finding the shortest paths, IS-IS ensures optimal routing and efficient use of network resources.
Routing Table Calculation: Based on the information in the link-state database, IS-IS routers populate their routing tables with entries for reachable destinations. The routing table contains the next-hop router and the interface through which data packets should be forwarded to reach each destination. Routers use this information to make forwarding decisions and route data packets through the network.
Hierarchical Design: IS-IS networks are often organized into a hierarchical structure, similar to OSPF. Routers are grouped into areas, with each area representing a logical subset of the network. This hierarchical design helps manage the complexity of large networks and improves scalability and performance.
Unique Aspects of IS-IS:
Protocol Independence: One of the unique features of IS-IS is its protocol independence. Unlike some other routing protocols that are tied to specific network layer protocols (such as IP), IS-IS can operate with various network layer protocols, including IP, IPv6, and OSI CLNS (Connectionless Network Service). This flexibility makes IS-IS suitable for diverse network environments and allows it to support multiple protocols simultaneously.
CLNS Support: IS-IS was initially developed for the OSI protocol suite and is widely used in networks that adhere to OSI standards. It provides native support for CLNS, allowing routers to exchange routing information and route data packets based on OSI addresses. While OSI never gained widespread adoption, IS-IS remains a popular choice for networks that utilize OSI protocols.
Fast Convergence: IS-IS is known for its fast convergence time, particularly in large-scale networks. When changes occur in the network, such as link failures or topology changes, IS-IS routers quickly recalculate their routing tables and converge to optimal routes. This rapid convergence ensures minimal disruption to network traffic and improves network reliability.
Scalability: IS-IS is highly scalable and can support networks of varying sizes, from small office networks to global telecommunications networks. Its hierarchical design, efficient link-state database synchronization, and support for route summarization contribute to its scalability and make it suitable for networks with thousands of routers and links.
Traffic Engineering: IS-IS supports traffic engineering capabilities, allowing network administrators to control the flow of traffic through the network. By manipulating routing metrics and adjusting link costs, administrators can influence the paths that data packets take, optimizing network performance and resource utilization. Traffic engineering features are particularly useful in large networks with complex traffic patterns.
Multi-Topology Routing: IS-IS supports multi-topology routing, which allows routers to maintain multiple separate routing topologies within the same network. Each topology represents a different set of routing information, such as IP routes, IPv6 routes, or traffic engineering metrics. Multi-topology routing enables routers to support diverse services and applications within the network while maintaining logical separation between them.
Security Features: IS-IS includes built-in security features to protect routing information and prevent unauthorized access to the network. These features may include authentication mechanisms, cryptographic algorithms, and access control lists (ACLs) to ensure the integrity and confidentiality of routing updates. By securing routing information, IS-IS helps mitigate the risk of routing attacks and unauthorized network access.
Conclusion:
Intermediate System-to-Intermediate System (IS-IS) is a versatile and robust routing protocol that plays a crucial role in modern computer networks. With its protocol independence, support for OSI CLNS, fast convergence, scalability, and advanced features such as traffic engineering and multi-topology routing, IS-IS offers network administrators a powerful tool for building and managing complex networks.
Whether used in ISP backbones, telecommunications networks, or enterprise environments, IS-IS provides efficient and reliable routing solutions for networks of all sizes and configurations.
BORDER GATEWAY PROTOCOL (BGP)
Introduction to Border Gateway Protocol (BGP):
Imagine the internet as a vast network of roads connecting different cities and towns. Now, think of Border Gateway Protocol (BGP) as the system of signs and signals guiding traffic across these roads. BGP is like the traffic manager of the internet, directing data packets to their destinations efficiently and securely. In this guide, we’ll break down BGP into easy-to-understand concepts, explore its role in the internet’s infrastructure, and uncover its unique features.
What is BGP?
Border Gateway Protocol (BGP) is a routing protocol used to exchange routing information between autonomous systems (ASes) on the internet. Think of ASes as individual neighborhoods within a city, each managed by its own network administrator or organization. BGP enables routers within these ASes to communicate with each other and make routing decisions based on the most efficient paths to reach destinations outside their own network.
How Does BGP Work?
Path Vector Protocol: BGP is a path vector protocol, which means it considers multiple factors when making routing decisions, including the path length, policy constraints, and network policies. Unlike other routing protocols that focus solely on finding the shortest path, BGP takes into account various attributes associated with each route to determine the best path.
Autonomous Systems (ASes): BGP operates between autonomous systems, which are individual networks or groups of networks that operate under a single administrative domain. Each AS has its own unique identification number called an Autonomous System Number (ASN). BGP routers within an AS exchange routing information with routers in other ASes to facilitate data communication across the internet.
BGP Peering Relationships: BGP routers establish peering relationships with routers in other ASes to exchange routing information. These peering relationships can take different forms, including:
Internal BGP (iBGP): Routers within the same AS exchange routing information using internal BGP sessions. iBGP ensures that all routers within the AS have consistent routing information.
External BGP (eBGP): Routers in different ASes exchange routing information using external BGP sessions. eBGP allows ASes to communicate with each other and share routing information across the internet.
BGP Attributes: BGP routes are associated with various attributes that describe their characteristics and preferences. Some common BGP attributes include:
AS Path: The sequence of AS numbers that a route has traversed to reach a destination. BGP routers use AS path information to avoid loops and select the best path.
Next Hop: The IP address of the next router in the path to reach the destination. BGP routers use the next-hop attribute to forward data packets along the selected path.
Weight: A local preference value assigned to a route by a BGP router. Weight is used to influence routing decisions within the AS.
Local Preference: A BGP attribute used to determine the preferred exit point for outbound traffic within an AS.
Multi-Exit Discriminator (MED): An attribute used to influence routing decisions between different ASes.
Community: A tag or label attached to a route to indicate specific policies or preferences.
Route Advertisement and Selection: BGP routers advertise routes to their neighbors and select the best routes based on various criteria. When receiving multiple route advertisements for the same destination, BGP routers compare the attributes associated with each route and select the route with the best combination of attributes. BGP routers then update their routing tables accordingly and use the selected routes to forward data packets.
Path Selection Process: BGP routers use a complex path selection process to determine the best path for each destination. This process involves comparing the attributes of available routes and applying policy constraints specified by the network administrator. The path selection process ensures that BGP routers make informed routing decisions based on network policies and preferences.
Unique Aspects of BGP:
Policy-Based Routing: BGP allows network administrators to implement policy-based routing, where routing decisions are based on specific policies or criteria. Administrators can define policies to control the flow of traffic, influence route selection, and implement security measures. Policy-based routing gives administrators granular control over how traffic is routed through the network, allowing them to optimize performance and ensure compliance with organizational policies.
Path Attributes and Manipulation: BGP provides extensive support for path attributes, allowing administrators to manipulate routing decisions based on various criteria. By adjusting attributes such as AS path, next hop, and local preference, administrators can influence route selection and traffic flow. Path attribute manipulation is a powerful tool for optimizing routing in complex networks and implementing traffic engineering solutions.
Route Aggregation and Summarization: BGP supports route aggregation and summarization, allowing administrators to reduce the size of routing tables and minimize the amount of routing information exchanged between routers. Aggregating multiple routes into a single summary route reduces the overhead associated with routing updates and improves network scalability. Route summarization is particularly useful in large networks with complex topologies, where it can help streamline routing and conserve network resources.
Communities and Route Tagging: BGP introduces the concept of communities, which are tags or labels attached to routes to convey specific information or policies. Communities allow administrators to classify routes based on common characteristics or preferences and apply policies consistently across the network. By tagging routes with communities, administrators can implement complex routing policies and traffic engineering solutions with ease.
Route Filtering and Policy Enforcement: BGP routers support route filtering and policy enforcement capabilities, allowing administrators to control which routes are advertised or accepted by their routers. By applying filters based on route attributes, administrators can prevent the propagation of undesirable routes, enforce security policies, and protect against routing anomalies. Route filtering and policy enforcement are essential for maintaining the integrity and stability of the BGP routing infrastructure.
BGP Security: BGP includes features to enhance the security and reliability of the routing infrastructure. These features include mechanisms for authentication, route validation, and secure communication between BGP routers. By implementing security measures such as cryptographic authentication and route validation, administrators can protect against route hijacking, unauthorized route injection, and other security threats. BGP security is essential for maintaining the trustworthiness of the global routing system and ensuring the integrity of internet routing.
BGP Communities and Internet Exchange Points (IXPs): BGP communities play a crucial role in the operation of Internet Exchange Points (IXPs), which are physical locations where multiple networks connect to exchange traffic. IXPs use BGP communities to facilitate traffic exchange between participating networks and implement policies for traffic routing and peering. By tagging routes with communities, IXPs can classify traffic based on destination, source, or quality of service requirements, enabling efficient and reliable traffic exchange between networks.
Global Routing Policy and Coordination: BGP facilitates global routing policy and coordination by enabling network operators to exchange routing information and negotiate routing agreements. Through bilateral peering agreements, multilateral peering arrangements, and regional or global routing registries, network operators coordinate their routing policies and ensure consistent routing behavior across the internet. Global routing policy and coordination are essential for maintaining the stability, reliability, and interoperability of the global routing system.
Conclusion:
Border Gateway Protocol (BGP) is a critical component of the internet’s routing infrastructure, enabling routers to exchange routing information and make informed routing decisions. By providing a flexible and scalable routing framework, BGP supports the growth and evolution of the internet and facilitates efficient communication between autonomous systems.
With its unique features such as policy-based routing, path attribute manipulation, and route aggregation, BGP empowers network administrators to optimize routing performance, implement traffic engineering solutions, and enforce security policies. As the backbone of the internet’s routing system, BGP plays a vital role in ensuring the reliability, stability, and security of global communication networks.
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
routing protocols routing protocols routing protocols routing protocols
I am truly thankful to the owner of this web site who has shared this fantastic piece of writing at at this place.
Pretty! This has been a really wonderful post. Many thanks for providing these details.